The cryptocurrency landscape, with its promise of decentralization and financial freedom, has attracted innovators, investors, and, unfortunately, a new breed of cybercriminals. Among them is Yahya Maghrab, a Canadian teenager born on April 27, 2007, who initially presented himself as a credible entrepreneur contributing to reputable platforms like Benzinga and Youth Ki Awaaz. On social media, particularly X (formerly Twitter), Maghrab crafted an image of a successful digital marketer based in Miami, Florida, boasting connections with over 500,000 individuals. This carefully curated persona suggested legitimacy and ambition, masking a darker reality. In 2023, a meticulous investigation by crypto sleuth ZachXBT unmasked Maghrab as a key figure in a series of SIM swap attacks that siphoned over $4.5 million from victims, primarily in the United States. His case highlights the alarming accessibility of cybercrime to young individuals and exposes vulnerabilities in the cryptocurrency ecosystem, raising urgent questions about security, regulation, and trust.
Maghrab’s alleged criminal activities center on SIM swap attacks, a sophisticated form of cybercrime that exploits the reliance on SMS-based two-factor authentication (2FA). By convincing telecommunications providers to transfer a victim’s phone number to a SIM card controlled by the attacker, cybercriminals gain access to sensitive accounts, including email, social media, and, most critically, cryptocurrency wallets. Maghrab’s role in these schemes was pivotal: he conducted detailed lookups on X accounts to identify high-value targets, passing this information to his accomplice, Skenkir, who executed the SIM swaps. In some instances, Maghrab directly orchestrated the attacks, collaborating with another scammer, HZ, to maximize their illicit gains. The scale of their operations, which targeted prominent crypto figures and projects, underscores the audacity and sophistication of their methods, as well as the devastating financial impact on victims.
The unraveling of Maghrab’s public image began with ZachXBT’s investigation, which linked him to over 17 SIM swap attacks responsible for stealing more than $4.5 million. These attacks targeted individuals and entities deeply embedded in the crypto and NFT communities, exploiting their trust in digital platforms. The investigation revealed a pattern of calculated deception, with Maghrab leveraging his access to data tools to identify vulnerable accounts and facilitate attacks. His collaboration with Skenkir and HZ, both implicated in criminal activities, further amplified the scope of their operations. The case not only exposes Maghrab’s role in these heists but also highlights broader systemic issues in the cryptocurrency industry, including inadequate security practices and the challenges of prosecuting international cybercriminals.

Maghrab’s Deceptive Persona and Rise to Infamy
Yahya Maghrab’s public persona was a masterclass in deception, blending youthful ambition with a veneer of legitimacy. At just 16 years old, he contributed articles to Benzinga, a financial news platform, and Youth Ki Awaaz, an Indian youth-oriented outlet, positioning himself as an emerging voice in digital marketing and entrepreneurship. His X profile, before its deletion, portrayed him as a Miami-based professional with a vast international network, claiming connections with over half a million individuals. This image of success and connectivity was designed to inspire trust, making Maghrab appear as a credible figure in the business world. Behind this facade, however, he was allegedly orchestrating a series of cybercrimes that would shock the crypto community.
The turning point came in October 2023, when ZachXBT, a pseudonymous crypto investigator renowned for exposing blockchain fraud, published a detailed exposé on X. The investigation revealed Maghrab’s involvement in SIM swap attacks that targeted high-profile crypto figures and projects, resulting in losses exceeding $4.5 million. ZachXBT’s findings, supported by blockchain analysis and screenshots of Maghrab’s communications, painted a damning picture of a teenager who exploited his technical skills and access to data tools to facilitate devastating thefts. The revelation shattered Maghrab’s carefully crafted image, exposing him as a central figure in a criminal network that preyed on the vulnerabilities of the crypto ecosystem.
Maghrab’s ability to operate under the radar for so long highlights the challenges of detecting cybercrime in the digital age. His contributions to legitimate platforms like Benzinga and Youth Ki Awaaz lent him an air of credibility, while his social media presence amplified his reach. The deletion of his X account and other online profiles following ZachXBT’s investigation suggests a calculated attempt to erase his digital footprint, a common tactic among cybercriminals seeking to evade detection. This duality—between Maghrab’s public persona and his alleged criminal activities—underscores the ease with which young individuals can exploit the anonymity and decentralization of the internet to perpetrate sophisticated scams.
The Mechanics of SIM Swap Attacks
SIM swap attacks, the cornerstone of Maghrab’s alleged crimes, are a potent form of cybercrime that exploit weaknesses in telecommunications and account security systems. The process begins with the attacker gathering personal information about a target, often through social media or data breaches. This information is used to convince a phone carrier to transfer the victim’s phone number to a new SIM card controlled by the attacker. Once the number is compromised, the attacker intercepts SMS-based 2FA codes, gaining access to the victim’s accounts. In the context of cryptocurrency, this access is particularly devastating, as it allows attackers to drain wallets containing valuable digital assets.
Maghrab’s role in these attacks was to conduct lookups on X accounts, identifying targets with significant crypto holdings. Using specialized data tools, he extracted phone numbers linked to these accounts, which he then passed to Skenkir, the primary executor of the SIM swaps. This division of labor allowed the group to operate efficiently, targeting individuals and entities with high-value assets. In some cases, Maghrab took a more active role, coordinating attacks and splitting the proceeds with his accomplices. The scale of their operations, which spanned multiple high-profile incidents in 2023, demonstrates the sophistication and audacity of their approach.
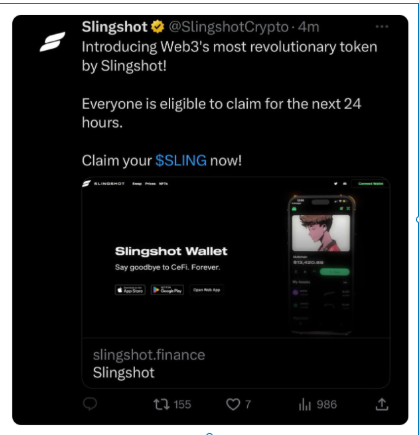
The financial impact of these attacks was staggering. The Gutter Cat Gang attack on July 7, 2023, resulted in losses exceeding $720,000, with Maghrab pocketing $250,000 from four transactions linked to a flagged wallet address. The Bitboy Crypto attack on June 10, 2023, saw losses of $950,000, though Maghrab received no payment due to a betrayal by another scammer, Smoke, who absconded with the funds. The Slingshot Crypto attack on June 19, 2023, incurred losses of $36,000, with Maghrab earning $9,700. Perhaps the most egregious was the July 19, 2023, attack on PleasrDAO core team member Jamis, who was recovering from a traumatic brain injury. This incident resulted in losses exceeding $1.3 million, including $807,000 in MAGIC tokens, with Maghrab’s share amounting to $144,000. These incidents, among others, highlight the devastating consequences of Maghrab’s actions and the vulnerability of even prominent figures in the crypto space.
Collaboration with Accomplices and Additional Scams
Maghrab’s criminal activities extended beyond SIM swap attacks, as he collaborated with accomplices to execute additional scams. One notable scheme involved a “panel scam” in July 2023, where Maghrab and HZ defrauded a victim named Amir of 136 ETH, equivalent to $250,000 at the time. The duo falsely claimed to be selling access to Maghrab’s data panel, a tool used to identify targets for SIM swaps. The scam inadvertently exposed Maghrab’s wallet address, which ZachXBT later used to link his various activities. The stolen funds were split evenly between Maghrab and HZ, demonstrating their close partnership.
HZ, a known scammer whose assets were previously seized by the FBI, brought additional notoriety to the group. Following his arrest, law enforcement confiscated significant assets, including a Bored Ape Yacht Club NFT, luxury watches, and a Doodle NFT, validating the allegations against the duo. Maghrab’s association with HZ and Skenkir, both implicated in criminal activities, raises serious concerns about his network and the extent of his involvement in the crypto underworld. The panel scam, combined with the SIM swap attacks, illustrates the multifaceted nature of Maghrab’s operations, which leveraged technical expertise, social engineering, and insider connections to maximize illicit gains.
The collaboration between Maghrab, Skenkir, and HZ was marked by a clear division of roles. Maghrab’s expertise in data lookups provided the critical first step, identifying high-value targets. Skenkir’s execution of SIM swaps turned this information into actionable thefts, while HZ’s involvement in scams like the panel fraud added another layer of criminality. This synergy allowed the group to operate with alarming efficiency, targeting a range of victims from crypto influencers to NFT collectives. The financial rewards, often split as percentages of the stolen funds, incentivized their continued collaboration, even as their actions drew increasing scrutiny from investigators like ZachXBT.
Anti-Money Laundering and Reputational Risks
Maghrab’s handling of stolen cryptocurrency, particularly over 390 ETH valued at approximately $720,000, poses significant anti-money laundering (AML) risks. The decentralized and pseudonymous nature of blockchain transactions makes it challenging to track illicit funds, as attackers can disperse assets across multiple wallets and exchanges. Maghrab’s wallet address, identified by ZachXBT as 0x7da33a98247b584b0070355881be9085126b53e1, was linked to numerous fraudulent transactions, highlighting the difficulty of enforcing AML regulations in the crypto space. The ability to launder stolen funds through mixers, swaps, and obscure exchanges underscores the need for enhanced blockchain forensics and regulatory oversight.
The reputational risks associated with Maghrab’s actions extend beyond his personal downfall. Platforms like Benzinga and Youth Ki Awaaz, which published his contributions, face potential damage due to their association with a now-disgraced figure. While these outlets likely had no knowledge of his criminal activities, their vetting processes may come under scrutiny, raising questions about the due diligence applied to contributors. The broader crypto industry also suffers, as high-profile thefts erode public trust and fuel perceptions of the sector as a haven for fraud. Maghrab’s case exemplifies how individual actions can have far-reaching consequences, undermining the credibility of both institutions and the ecosystem they operate within.
Red Flags and Warning Signs
Several red flags in Maghrab’s behavior point to his illicit activities and attempts to evade accountability. The deletion of his X account and other online profiles is a telltale sign of someone seeking to erase their digital footprint, a common tactic among cybercriminals facing exposure. This move, while intended to obscure his actions, only heightened suspicion, as it coincided with ZachXBT’s investigation. The absence of an online presence makes it harder for investigators to track his current activities, but it also serves as a warning to others about the impermanence of digital identities in the face of scrutiny.
Maghrab’s lavish spending, despite his young age, is another glaring red flag. Reports of purchases including high-end watches and unreleased tracks from the late Juice WRLD suggest access to substantial illicit funds, far exceeding the income of a typical 17-year-old entrepreneur. Such conspicuous consumption, often flaunted on social media, is a hallmark of cybercriminals seeking to project success while ignoring the legal risks. Maghrab’s association with known scammers like Skenkir and HZ further compounds these concerns, as his network reveals a pattern of collaboration with individuals already under law enforcement scrutiny.
The combination of these red flags—deleted profiles, luxury spending, and ties to criminals—creates a clear picture of Maghrab’s intent to operate outside the bounds of legality. These warning signs, while evident in hindsight, highlight the need for greater vigilance among platforms, investors, and regulators in identifying and addressing potential threats before they escalate.
Legal Status and Investigative Challenges
As of March 22, 2025, there is no direct evidence of criminal proceedings against Yahya Maghrab, though the arrest of his accomplice HZ suggests that law enforcement is actively targeting their network. The complexity of international cybercrime cases, particularly those involving cryptocurrency, poses significant challenges for investigators. Jurisdictional issues, the anonymity of blockchain transactions, and the difficulty of tracing funds across borders often delay legal action. Maghrab’s wallet address, which received over 390 ETH from illicit transactions, remains a critical lead for authorities, but the decentralized nature of crypto complicates efforts to seize assets or prosecute offenders.
ZachXBT’s investigation has been instrumental in shedding light on Maghrab’s activities, providing detailed evidence that could aid law enforcement. The crypto sleuth’s ability to trace funds and expose wallet addresses demonstrates the power of blockchain forensics in combating crime. However, the lack of public updates on Maghrab’s legal status as of early 2025 suggests that investigations are ongoing, potentially hampered by the need to coordinate across multiple jurisdictions. The seizure of HZ’s assets, including high-value NFTs and luxury items, indicates that authorities are making progress, but Maghrab’s whereabouts and current activities remain unclear.
The broader context of crypto-related crime adds another layer of complexity. Recent cases, such as the U.S. Department of Justice’s 2024 crypto fraud sting and the sentencing of Evan Frederick Light for a $37 million theft, highlight the growing focus on combating digital asset fraud. Maghrab’s case, while smaller in scale, fits into this pattern of sophisticated cyberattacks targeting the crypto industry. The absence of formal charges against him may reflect the challenges of building a case against a young offender operating in a decentralized ecosystem, but it also underscores the urgency of developing new legal frameworks to address such crimes.
Implications for the Cryptocurrency Industry
The Yahya Maghrab case exposes critical vulnerabilities in the cryptocurrency ecosystem, particularly the reliance on SMS-based 2FA, which remains a weak link in account security. The ease with which attackers can exploit telecommunications systems to hijack phone numbers highlights the need for stronger authentication methods, such as hardware wallets and app-based 2FA. The targeting of high-profile figures like Bitboy Crypto and PleasrDAO’s Jamis also underscores the importance of educating crypto users about security best practices, including regular account monitoring and the use of cold storage for valuable assets.
From a regulatory perspective, Maghrab’s actions highlight the need for enhanced oversight of the crypto industry. The decentralized nature of blockchain transactions, while a strength, also enables criminals to operate with relative impunity. Governments and regulatory bodies, such as the U.S. Securities and Exchange Commission and the Financial Conduct Authority in the UK, must collaborate to develop frameworks that improve transparency, track illicit funds, and hold offenders accountable. The seizure of HZ’s assets demonstrates the potential for law enforcement to disrupt criminal networks, but more robust international cooperation is needed to address cases like Maghrab’s, which span multiple countries.
The reputational damage to the crypto industry is another significant concern. High-profile thefts, such as those orchestrated by Maghrab, reinforce perceptions of the sector as a risky and unregulated space. This can deter mainstream adoption and discourage institutional investment, slowing the growth of legitimate crypto projects. Platforms like Benzinga and Youth Ki Awaaz, inadvertently linked to Maghrab, face the challenge of restoring trust in their vetting processes, while the broader industry must grapple with the fallout of such scandals. Initiatives like ZachXBT’s investigations play a crucial role in fostering transparency, but they cannot replace the need for systemic reforms to protect users and deter crime.
Lessons and Recommendations
The Maghrab case offers several lessons for individuals, organizations, and regulators. For crypto users, the importance of robust security measures cannot be overstated. Avoiding SMS-based 2FA, using hardware wallets, and regularly monitoring accounts for suspicious activity are essential steps to mitigate risks. Investors should also exercise due diligence when engaging with crypto influencers or projects, verifying claims and researching the backgrounds of key figures. Maghrab’s youthful persona and contributions to legitimate platforms highlight how easily credibility can be fabricated in the digital age.
Organizations, particularly those in the crypto and media sectors, must strengthen their vetting processes to avoid association with individuals like Maghrab. Platforms like Benzinga and Youth Ki Awaaz should implement stricter contributor screening, including background checks and verification of claims, to protect their reputations. The crypto industry as a whole must invest in education and awareness campaigns to inform users about the risks of cyberattacks and the importance of secure practices.
Regulators face the challenge of balancing innovation with oversight. Developing international standards for tracking illicit crypto transactions, enhancing AML compliance, and streamlining cross-border investigations are critical steps to combat cybercrime. The success of efforts like the FBI’s seizure of HZ’s assets suggests that targeted interventions can yield results, but broader reforms are needed to address the root causes of crypto vulnerabilities.
Conclusion: A Wake-Up Call for the Crypto Ecosystem
Yahya Maghrab’s alleged role in stealing over $4.5 million through SIM swap attacks serves as a stark reminder of the vulnerabilities inherent in the cryptocurrency ecosystem. His ability to pose as a legitimate entrepreneur while orchestrating sophisticated cybercrimes highlights the ease with which young individuals can exploit the anonymity and decentralization of the internet. The collaboration with accomplices like Skenkir and HZ, combined with the targeting of high-profile figures like Bitboy Crypto and PleasrDAO, underscores the audacity and impact of his actions.
The case also exposes systemic issues in the crypto industry, from inadequate security practices to the challenges of prosecuting international cybercriminals. ZachXBT’s investigation has been instrumental in bringing Maghrab’s activities to light, demonstrating the power of blockchain forensics and community-driven accountability. However, the lack of direct legal action against Maghrab as of March 2025 suggests that significant hurdles remain in bringing such offenders to justice.
Ultimately, the Yahya Maghrab saga is a wake-up call for the crypto community. It underscores the urgent need for stronger security measures, enhanced regulatory oversight, and greater transparency to protect users and maintain trust in the ecosystem. As cryptocurrencies continue to evolve, addressing these vulnerabilities will be critical to ensuring that the promise of decentralization is not overshadowed by the perils of cybercrime. Stakeholders are encouraged to remain vigilant, adopt robust security practices, and support efforts to build a safer and more accountable crypto future.







